In the past three years, security breaches in the digital world have always managed to grab attention around the globe. Facebook was embroiled in a controversy surrounding data breaches back in 2018. According to the research carried out by Identity Theft Research Center, the data breaches carried out this year so far have already exceeded last year’s record by 17%. Thus, having a robust system to protect one’s data from being misused has become the need of the hour. To solve this major issue, the Zero Trust Architecture model has arrived.
For more information on data breaches, you can visit our blog:-
Data Breaches – What You Need to Know About this Threat
The following sections will delve into the aspects including what is zero trust, its history, foundation, how to implement zero trust, zero-trust network access, and zero trust principles, and will also talk about zero trust vs vpn.
What is Zero Trust Architecture?
Zero Trust architecture is an initiative that empowers organizations to avoid data breaches. It is a system that sustains the basic principle of placing no trust in the inside or the outside of the organization’s network.
The technology is rooted in the idea of verification. The Zero Trust model is designed to avoid any security breaches in the digital environment regulating user-access control and offering threat management and prevention.
The History Behind This Zero Trust Model
Zero Trust was created in response to the increasing data breaches in the digital world. The creator John Kindervag, the principal analyst of Forrester Research, thumped the old-age belief that security models operated knowing that the inside of an organization is trustworthy and by extension, it is safe. Under the Zero Trust model, the popular belief is not to trust anyone and always verify. The new model recognizes that trust can be compromised under various circumstances and thereby it is vulnerable.
How does Zero Trust Architecture Work?
In this security system, companies have to define a shield that will act as a protective surface; that protection surface is composed of the company’s most important information, organizational assets, and services. The protection surfaces are different for all organizations as it contains critical data about a company’s operations. General examples are a two-factor authentication system and options for keeping me logged in or no cookies. Google developed its own zero-trust architecture called the BeyondCorp framework in response to the cyber attack on confidential data allegedly committed by the government of China in 2009.
After the protection surface is defined, you can track the flow of the organization’s data concerning the protection surface. It is very important to determine the flow of data and its users who access it. If the relation between operations, users, data, and services is understood, it is easier to apply zero trust architecture because then you can apply controls near the protection surface.
Thus, you will create microperimetry around the protection surface using a segmentation gateway (an advanced version of the firewall). This will ensure regulated access to the protective surface. The segmentation gateway brings regulated visibility to the data along with multiple layers of inspection and access control. This part is based on the Kipling method of defining who, why, what, when, where, and how. Thus, it determines who has access to the microperimetry and filters any unauthorized intervention.
Reasons for the deployment of Zero Trust Architecture in 2023
There are many advantages but the three core advantages are-:
1. Verify Every User
It helps in verifying users, determining data flows, anticipating calculated risks, and setting cookies policy. Zero Trust uses microsegmentation to operate which means it grants limited access to the users and not the complete network. Microsegmentation allows zero trust to authenticate each access request and avoid any unauthorized access.
2. Validate their Devices
Apart from this, it empowers companies to deploy next-generation firewalls including decryption capabilities. Based on continuous analysis and monitoring, zero trust uses the key identifiers and automates the accessibility process. This simplifies the process for the IT department as they are not involved in authenticating each request.
3. Limit their Access
One of the major reasons to use this architecture is to acquire visibility and context. Zero trust security is not satisfied with the username and password only. It requires context for its program to run. The advanced version of the firewall activates the segmentation of microperimetry and acts as a protective shield for the company. This is useful for the protection of the company data, especially streamlining and assigning tasks in remote working.
The Core Principles of Zero Trust System in 2023
six zero-trust principles in detail.
1. Constant Regulation and monitoring
The ethos of zero trust architecture is that trust is vulnerable and subjected to different interpretations under circumstances. Hence, no one the inside or the outside of the organization shall be trusted. The Zero Trust model determines the identities of the user, device, and flow of information. For instance, two-factor authentications and logins are valid for a limited period and users have to re-verify after a period of inactivity.
2. Regulated User Access
The next principle of zero-trust security is monitored access. It implies that users will get limited access, based on their needs. This keeps the system safe and ensures minimum exposure to other information stored on the system. It includes the management of user permissions.
3. Monitored Device Access
This is one of the lesser-known principles. It means that zero trust security regulates not only user access but applies controls to devices. Zero trust systems keep a track of the different devices that access their network and ensure that they do not tamper with security issues. These features further ensure the security of the data and the network.
4. Microsegmentation
Microsegmentation refers to the process of breaking security perimeters into fragments. This is done to maintain separate access for various parts of the network. For instance, a network with many files stored at a single data center would contain different safe zones. This regulates users’ access in a way that if anybody wants to access one zone, they would not be able to access the other without a distinctive authorization.
5. Restricts Lateral Movement
In lateral movement, it is difficult to determine the position of the hacker even after knowing its entry point. But in the case of zero security, because the data is stored in fragmented zones, it is hard for the hacker to access and navigate across different microsegments. So, when the attacker’s movement is detected, it is easier to cut it off from further damage.
6. Multi-factor Authentication
Multi-factor Authentication is at the heart of the zero-trust system. It means that knowing the password is not enough and more evidence will be required to access the file. The most common application of MFA is two-factor authentication used on Facebook and Google.
The Foundations of Zero Trust Architecture
Now that we have already studied what is zero trust architecture, it is the right time for us to get into the foundational structure.
1. Context-based identification and verification
This security is founded on context-based identity authentication, and policy verification that ensures that users have access only to the files they are granted for. This helps reduce cyber-attacks attempted due to lateral movement. This empowers organizations to keep track of unauthorized access and cyber-attacks.
2. Applications not visible on the internet
It is rooted in safety and regulated access to data that makes applications invisible for the sole reason of not revealing the organizational network to the internet including IP addresses and source identities. Thus, it ensures authorized access to the files upholding security and privacy concerns.
3. Proxy Architecture
Ensuring the security of data from any cyber threats requires a proxy architecture designed to analyze the data, manage real-time policies and monitor security decisions before letting data be moved to its final stage. All this has to be carried out without any impact on the performance irrespective of the users’ systems.
What is Zero Trust network access (ZTNA)?
Zero Trust Network Access (ZTNA) is at the core of the Zero Trust security system. It empowers organizations to adopt Zero Trust security in their networks. ZTNA does not reveal any details including IP addresses, infrastructure, and services. Zero trust network access is known for setting up encrypted connections between devices and resources. It is similar to the software-defined perimeter (SDP).
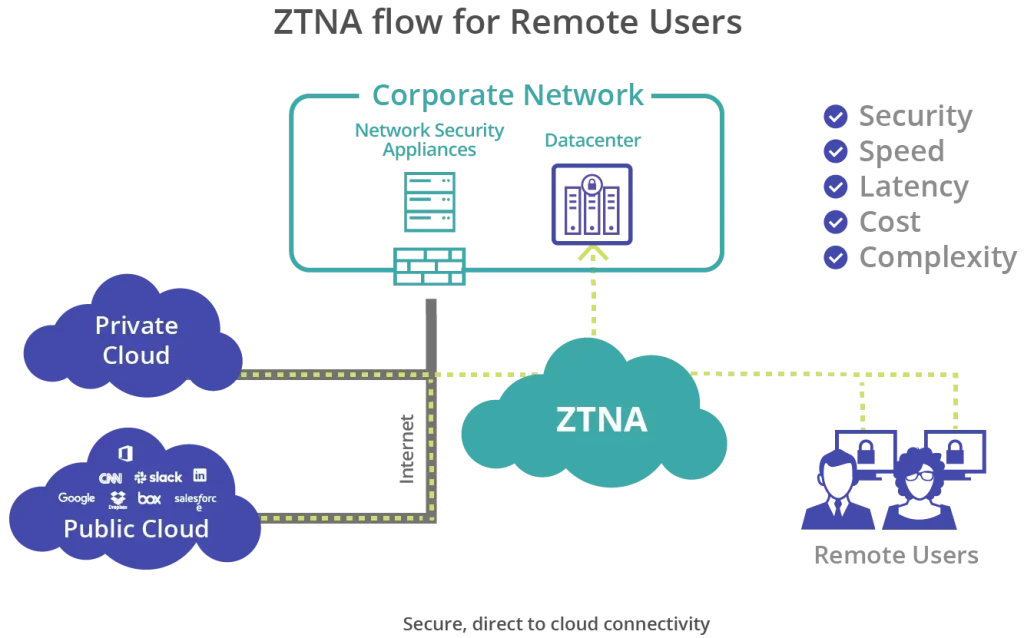
(Image Source: https://www.mcafee.com/)
How to implement Zero Trust Security System?
The implementation of a zero-trust network is not as complex as it may sound and also, it is a cost-effective technique to avoid any major losses from a security breach or any unauthorized access to the network. The adoption of this system involves five main steps that are listed below.
1. Network Segmentation
Segmentation of network and data is integral to zero trust security. It minimizes lateral movement and empowers organizations to regulate access to a limited number of people. All employees would not have access to the complete network but only a portion that is related to their work. This ensures the complete security of the data.
2. A Robust access management system
Another important factor in implementing a zero trust network is building a strong access management system. For instance, using multi-factor authentication. This would ensure regulated access as users would need more evidence other than a password to access the file.
3. Minimizing privilege at the firewall
This is useful for specific departments that do not require direct communication as they are operating remotely. In such cases, the cyber security department would enable access to those departments that need those files for their work.
4. Application Context to Firewall
The basic rule of a zero trust system is regulating access to all people, inside and outside of the organization. Adding to this, cyber teams have begun uploading application inspection technology to the current firewall. This ensures that any data passed over is authenticated and contains appropriate content.
5. Analyzing Security events
Cybersecurity analysts can work efficiently only when they have acquired data that can be used for drawing insights and conclusions. Hence, many organizations use security information and event management solution that helps them to draw the conclusion and correlations out of huge chunks of data.
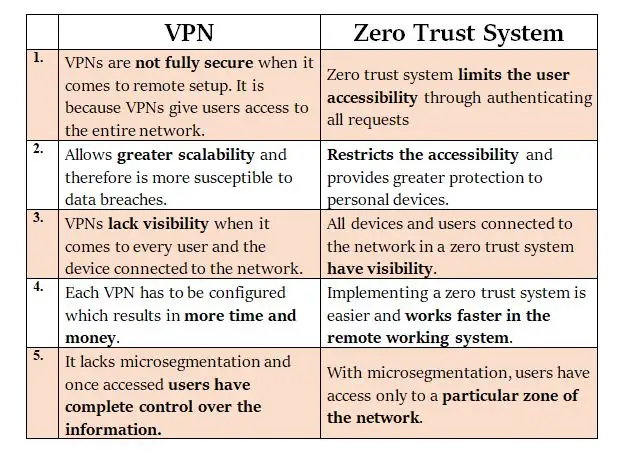
Difference between Zero Trust and VPN
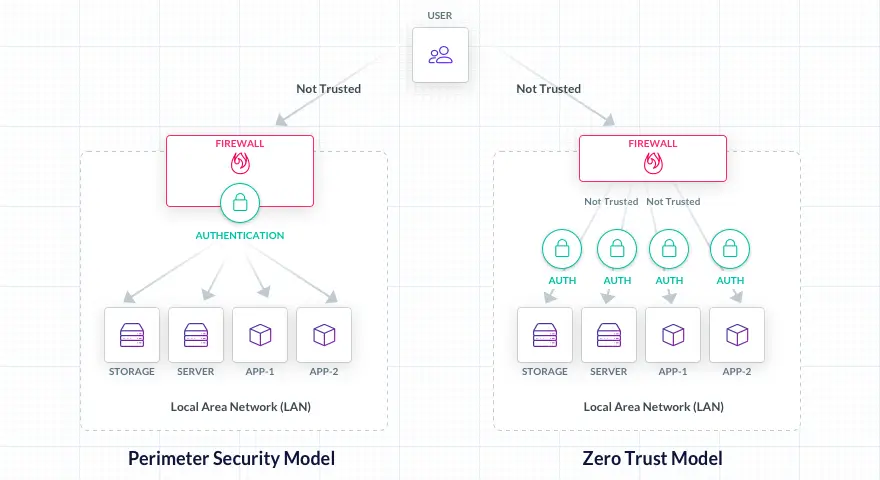
(Image Source: https://goteleport.com/)
VPN stands for Virtual private network that allows remote workers to have access to the company’s network from any place just as they had it from their office. Any place could be their home or a different branch location. This section is going to touch upon zero trust vs VPN.
VPN and Zero security model operate on a different basis. Zero trust sustains itself on the basic fundamental of zero trust capabilities and no one has complete access to the network. On the other hand, VPN allows network access to authorized remote employees and users. To avoid any security breaches, a Zero Trust model is a more useful technique for organizations in the time to come.
The tabular comparison between these two is given below:-
Conclusion
These systems have the potential to uncover apertures in traditional systems of security. With them, zero security has added a layer of complexity to a security framework in terms of network segmentation. Cyber teams must ensure those accurate authorizations are updated regularly. Zero security architecture is an extremely helpful system for large organizations that have complex and sensitive data. We hope this article has answered your questions!
Frequently Asked Questions (FAQs)
Ans: Regardless of their location or network, no person or device may be trusted by default according to the Zero Trust Architecture (ZTA) cybersecurity paradigm. Before allowing access to apps and data, ZTA continuously verifies people and devices. This aids in defending enterprises from a variety of cyberattacks, such as insider threats, ransomware assaults, and data breaches.
Ans: ZTA offers a number of benefits such as:
-Enhanced security: By supposing that no user or device can be trusted by default, ZTA helps to defend companies from a wider spectrum of threats.
-Better visibility: ZTA gives businesses a clearer picture of their IT infrastructure, which helps speed up the identification and mitigation of security issues.
-Cost savings: By removing the need for pricey perimeter security systems, ZTA may assist enterprises in saving money on security
Ans: There are several ways to implement ZTA, but the most popular method is to employ a mix of policy modifications, software, and hardware. Among the crucial elements of a ZTA implementation are:
–IAM: Before allowing access to apps and data, identity and access management (IAM) solutions may be used to confirm the identification of people and devices.
–Microsegmentation: Microsegmentation is a process that splits the network of an organization into tiny, independent parts. This aids in reducing the effect of a cyberattack should one take place.
-Continuous monitoring: Real-time detection and reaction to security risks is possible with the help of continuous monitoring systems.
Ans: Some of the key challenges of implementing ZTA include:
-Cultural shift: ZTA necessitates a shift in an organization’s culture. Training for the new security policies and procedures is required for the workforce.
-Cost: Setting up ZTA as a security framework might be expensive. Depending on the size and complexity of an organization’s IT infrastructure, deploying ZTA will cost a different amount.
-Complexity: Managing ZTA, a security framework, can be challenging. ZTA implementation and management need a thorough grasp of an organization’s IT architecture.
Ans: ZTA is a security framework that is continually evolving. ZTA is expected to become the default security architecture for businesses of all sizes as assaults get more sophisticated.