Cybercrime is the greatest threat to every company in the world.
– Ginni Rommety
Cybersecurity is one of those areas in our digital world where overconfidence does not bode well for users, developers, and website owners. No matter how “impregnable” your security protocols are, you need to be at the edge of your seat and up on your toes all at the same time for any vulnerability that may be exploited by cyberthieves.
Being ignorant of such attacks is even worse. Financial loss and identity theft result in these types of cyberattacks. In the figure below, we will see the top online banking vulnerabilities, most of which come from in-house applications making up 59% of the vulnerabilities.
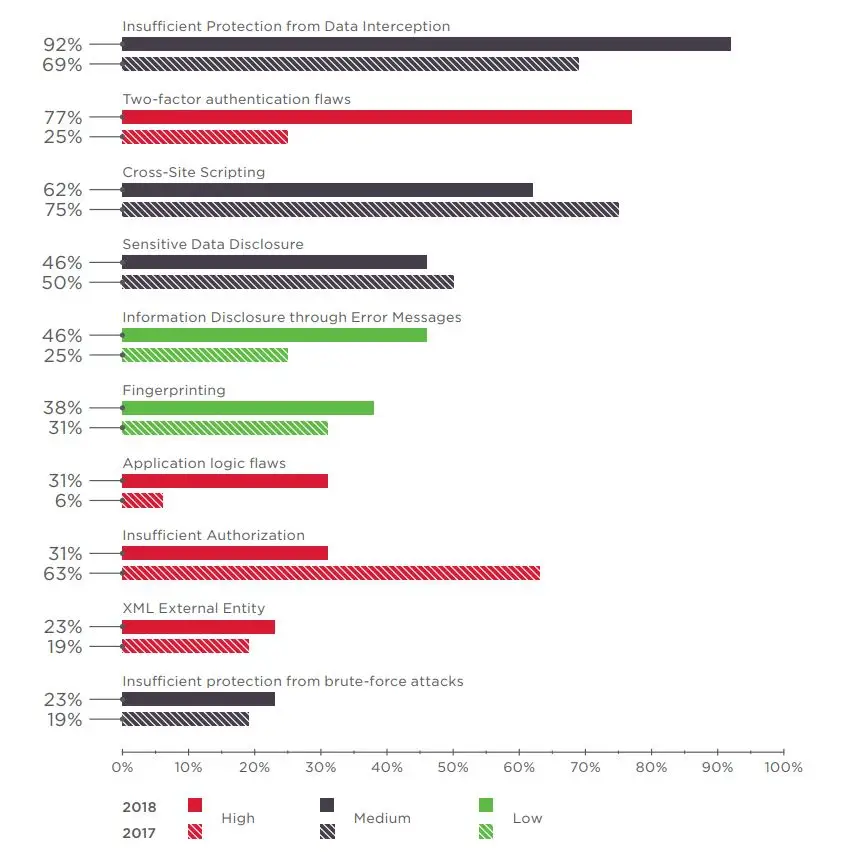
Image Source: Positive Technologies
Cybercriminals are relentless in exploiting the weaknesses in any system. Security experts have been on the defense to fend off these cybercriminals. Some of the most severe cyberattacks involved unbelievably massive data breaches in companies like Yahoo, Facebook, and even Google.
Hackers attack every 39 seconds, and on average of 2,244 times a day. Since 2018, security breaches have increased by 78%. In 2019, the average time to identify a data breach was 206 days out of the 314 days average lifespan of a data breach. 94% of these malware infections were delivered by email.
Did you know that 81% of confirmed data breaches are according to password weaknesses?
A data breach is the release of confidential information into an unsecured environment. It is also identified as information leakage, data spill, data leak, or unintentional data or information disclosure.
The Dangers of a Data Breach –
Ways How Hackers Can Breach System –
A Compromised Network
As was mentioned above, a hacker, with his exploit tools, only needs an open the door to gain entry to a secured network. Selling critical information on the dark web does not command a high price. But when the data is used, that is when the hacker’s profit. One way to open the door for a data breach is when an employee willingly discloses information into an unsecured network, thereby opening the door for the breach. Another way is an employee compromised the secured network by opening a document modified with malware. It leads us to the next way in which hackers gain entry to a secured network.

A Different Type of Human Error
With the ease of storing our data in different ways, people sometimes forget that they have critical data and information stored in a container that is only protected by a password and maybe a few security questions. Those with malicious intent can exploit a forgotten critical file in seldom-used storage. Most of us have experienced opening two windows wherein we are managing our personal social media site or even the company’s official site and also trying to send that critical file to a boss that needs it as soon as possible. With a simple click and drop on the wrong window or platform, an employee has compromised the network once data is copied and harvested.
“Passwords are like underwear: you don’t let people see it, you should change it very often, and you shouldn’t share it with strangers.”
– Chris Pirillo
Malware and Phishing Attacks
Through information campaigns, people have become more aware not to install EXE files from unknown sources. But phishing attacks have become clever and sophisticated over time. With the aid of Artificial Intelligence, hackers are developing phishing scams, schemes, and attacks that are almost indistinguishable from the real thing. The phishing attack’s objective is to trick and deceive a person. Most phishing attacks are made through email. Having a message that looks legit can make us complacent and trusting to “do as we are told.” That means we may click the link, open that document, or even install a file when told to do so. This compromises the security of your device, which then compromises your network opening it to further hidden, malicious visits to explore the servers and harvest critical data.
Cyber criminals can use personal details, such as your favorite color, the last four digits of your credit card and your email addresses, to make educated guesses about your sign-in credentials.
– Larry Alton

Insufficient Knowledge and Training to Defend against an Attack
All that is needed to compromise a network, whether it is an extensive one or simply small business network, is just an open door. That open door can be an employee that does not know how a phishing attack or scam looks like. That open door can also be the IT personnel that has little to no experience in cybersecurity or may have been lazy in updating and checking the network for unusual traffic. That open door can also be that overconfident owner that bought a costly cybersecurity software but did not train the staff to update their software to patch up any vulnerability in their system.
IOT without security = Internet of threats
– Stephane Nappo
Some Biggest Data Breaches Attack Examples
Yahoo
Yahoo’s data security team discovered an intrusion on their systems and access sensitive data. At this point, Yahoo thought that hackers have accessed and stolen information of around 500 million users. This number continued to rise throughout the following years. In 2016, Yahoo had announced that breach compromised all 3 billion user accounts of the company.

Facebook, experienced severe data breach when a collection of databases was found online containing around 419 million users’ information. According to TechCrunch, another set of databases was found to contain information of 133 million US-based Facebook users, 18 million UK-Based Facebook users and 50 million Vietnam-based Facebook users.
“It takes 20 years to build a reputation and few minutes of cyber-incident to ruin it.”
— Stephane Nappo
Marriott International and Starwood Hotels
Marriot International announced last November 2018 that hackers were able to infiltrate and steal sensitive information of their customers that amounted to around 500 million.
Marriot International acquired a hotel brand known as Starwood in 2016. The infiltration already happened way back in 2014, but the breach was only detected around September 2018. They found out that the breach affected only those guests that made a reservation through a Starwood hotel property.
Equifax
Equifax got infiltrated around May 2017 through an application vulnerability that compromised the data of around 148 million consumers. Equifax data breach was found in the last week of July 2017. The files that were compromised included birth dates, driver’s license numbers, and social security numbers. The credit card data of 209,000 account holders were also exposed.
eBay
eBay’s user database was breached and was reported in May 2014, when corporate employees’ accounts were breached by attackers who used these accounts to have access to eBay’s system for 229 days. The number of affected users was around 145 million. The corporation sent a notice for users to change their passwords immediately to abet the attack.
Here is a video of 25 of the most significant and most severe data breaches of all time.
Conclusion: Learn from the Past and Get Smarter Protection
Learning from the past behaviors of data breach attackers can help us better protect ourselves, our data, and our online transactions. It is also a great reminder that we cannot be casual with our cybersecurity. We all should be aware of all data breaches and exactly what information we are sharing with the world without even us realizing it.
As we have seen from the examples above, sometimes hackers exploit every vulnerability they can find in a system to carry out data breach upon the entire network. Know how malware and antiviruses work and study other strategies that attackers use to breach into systems. Keeping all vulnerabilities secured is the first step to defense. In cybersecurity, prevention is always the best kind of protection.