The value of cryptocurrency continues to skyrocket in today’s times. This has given rise to a form of cybercrime that involves the threat of stealing cryptocurrency from different systems commonly known as ‘cryptojacking’. In this article, we are going to discuss what is cryptojacking, what is crypto mining, the rise of cryptojacking, cryptojacking examples, and how can it be prevented.
What Is Cryptojacking?
Cryptojacking definition is a form of crime committed in the cyber world involving unauthorized access to catch hold of cryptocurrencies. Everyone is aware of the value of cryptocurrencies in the present era which is why it makes it even vulnerable to get them stolen from somebody’s computer system.
Like any other cybercrime, cryptojacking is solely committed for profit. However, unlike other cybercrimes, cryptojacking is designed in a way that is completely hidden from the victim.
What Is Cryptocurrency Mining?
Cryptojacking is a cybercrime committed to mine cryptocurrencies. Owing to the growing value of cryptocurrencies, mining them proves to be a lucrative source of money. The phenomenon of earning cryptocurrencies by solving cryptographic equations using computers is called cryptocurrency mining.
The phenomenon is a bit complex and involves data blocks and blockchain. It includes all records right from transactions to public records (ledger), popularly called a blockchain. Thus, cryptojacking is a legal terminology that manifests the act of mining cryptocurrencies through illegal means. After learning about cryptojacking meaning and cryptocurrencies, let us see what led to the rise of crypto malware.
The Rise Of Cryptojacking
The first known bitcoin mining malware incident was reported in September 2017 when Bitcoin was achieving new heights in terms of its market value. Coinhive was the pioneer in providing cryptojacking services that allowed website owners to earn additional income from their visitors. Coinhive was a set of JavaScript files that used visitors and users’ resources to mine cryptocurrency for the owner.
Even after an unexpected fall in the value of cryptocurrency in the market in 2018, bitcoin witnessed a surge in midyear and skyrocketed the price of Monero. This reaffirmed the cyber criminals trust in monero as it cannot be tracked publicly and led to the rise of cryptojacking.

( Source- https://giphy.com/looneytunesworldofmayhem)
Another major reason behind the sudden rise of cryptojacking is produces more money than malware and ransomware for cyber criminals. Also, companies have tightened their security systems and they are no longer susceptible to malware and ransomware.
Malware attacks have witnessed a sudden drop in October 2019 and so is the case with ransomware. The following section will deal with the working of cryptojacking.
How Does Cryptojacking Work?
In simple words, cryptojacking begins with a user clicking on an unknown link which grants a hacker unauthorized access to its computer power to generate cryptocurrency. As part of cryptojacking, the user unintentionally downloads malicious software that grants cyber criminals access to their computing systems.
Before learning how cryptojacking attack works, we must be aware of how cryptocurrency files are spread by cybercriminals. It is important to know that crypto mining software is flagged as malware in some cases which is why they go undetected.
It primarily involves five main steps-
- Embedding crypto malware code into the system. This compromises the privacy of the computer system.
- The next step is running the cryptomining script in the system. In usual circumstances, the unsuspecting users run the script by clicking on clicking on unknown attachments or links.
- After clicking on the links, the user is totally unaware of the fact that the script continuously runs in the background.
- The script then uses the device to solve complex algorithms. After the algorithm is solved, blocks are mined which store digital information about cryptocurrency.
Cryptojackers receive cryptocurrency coins when they add a new block to the chain. Once received access to the reward, hackers directly put it into their digital wallets
Various Cryptojacking Methods
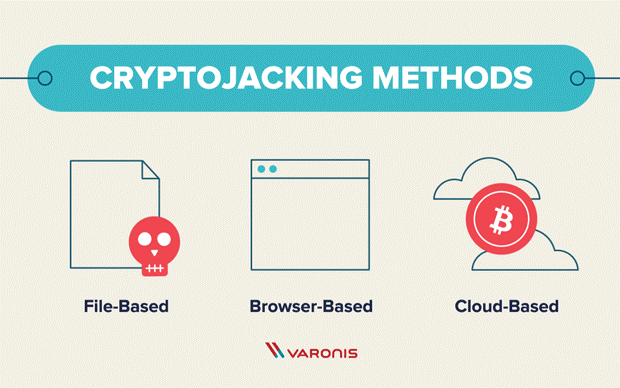
(Image source: https://blogvaronis2.wpengine.com/)
1. File-based cryptojacking:
The first method is file-based cryptojacking. This involves sending malicious emails which contain attachments or link that seems legitimate.
On clicking, the code gets executed, and it downloads the crypto mining script onto the computer system. The user remains completely unaware about the working of the script in the background and it runs continuously.
2. Browser-based cryptojacking:
Another method is browser-based cryptojacking. In this method, hackers create a cryptojacking script and embed it onto multiple browsers.
The cryptomining script uses a programming language and runs once the code is downloaded. In addition, these scripts can be embedded in ads as well as WordPress plugins.
3. Cloud cryptojacking:
Cloud Cryptojacking is one of the most difficult methods but if cracked it gives hackers absolute access to a company’s files and CPU resources.
To get access to an organization’s CPU systems and cloud services, cryptominers go through the codes and files for API keys. Once successful, hackers can siphon loads of confidential data and cryptojack important information for currency.
Real-world Examples
The cryptocurrency mining examples provided here are quite recent. The instances reveal major security lapses or blatant ignorance on the part of the victims/companies.
- As per a report of 2019, eight applications were secretly operated to mine cryptocurrency. Applications were later emitted from the Microsoft Store. The apps did reach their potential targets through keyword searches. When the potential target downloaded and launched the app, it would automatically download the JavaScript code used for the cryptojacking attack. The attacker then activated the code, used the device through unauthorized access, and began searching for Monero. In total, it was reported that there were three separate developers. However, all three developers were suspected to be either an individual or a group belonging to the same organization.
- Another example of cryptomining is Kobe Bryant’s image that was widely circulated in the media following the sudden death of the basketball player in a helicopter crash. Cryptominers hid the code using steganography which is why online users couldn’t catch it at once. It was an HTML file that led users to a website that run a cryptojacking script and mined Monero for the attackers.
- In 2018, Tesla’s AWS cloud system” was cryptojacked by cybercriminals for cryptocurrency mining. This was revealed by RedLock, a cyber security firm. It came as a shock as Tesla is a large company with strict security protocols in place. However, it was revealed that the attackers had plans of mining the Kubernetes console and later they got to know it belonged to Tesla. Kubernetes console was not password protected which is why cybercriminals were able to infiltrate into the system.
Why Is Cryptojacking Gaining Momentum?
There is no doubt about the immense popularity of cryptojacking software in the technological world. There is an article by Jason Bloomberg on Forbes that says that “cryptojacking has replaced ransomware as being the most popular cyber threat in the world”. There are a few technical reasons behind this. First, the software that cryptojacking runs on does not need to establish any link or command with the attacker.
Secondly, crypto mining software is flagged as malware and runs undetected. The only “visible” harm it might do is slow down the system. Thus, cryptojacking is committed by attackers as it mints money without going undetected by the users.
Ways To Detect Cryptojacking
It is hard to determine whether the device is being used for cryptocurrency mining as in many cases it goes undetected. However, there are certain markers that users can be mindful of and know if their device is being accessed by any third party without the owner’s consent.
- Excessive heating: Running the JavaScript code for crypto malware requires a lot of computing resources which might lead to excessive heating of the devices. Users can be mindful of this development and determine if something usual is happening.
- Monitoring CPU usage: If the users come across a usual jump in their CPU usage, it might be a marker of their device being accessed by a third party or undetected software is being run on their system.
- Activate security software for malware detection: Crypto mining software is flagged as malware which makes it all the more important for systems to have software for malware detection Malwares are used for infecting computers, having access to encrypted files, and trading bitcoins. Scanning your computer or any device for malware is a helpful step for how to detect crypto mining malware.
Tips To Prevent Cryptojacking
A strong and aware IT team is the most important aspect of preventing crypto malware. Being aware of the recent trends in cryptojacking can be extremely effective as it would help you know what the cybercriminals are up to. This section will provide you with an overview of how to prevent cryptojacking.
- Block pages that are known for using cryptojacking codes. Users companies can be mindful of the pages they access to. There are instances where some websites and pages are known for delivering cryptojacking codes to access people’s devices.
- Ad Blockers: Using adblocker applications is an effective way of filtering which ads or websites can appear on the screen. Ad blockers can detect and block pages/websites if they suspect any malicious code be used by them.
- Installing a cyber security program: It is extremely important, especially for big companies that have large accumulated data to have a cyber security program in place. In this article, we saw how a big company like Tesla was caught off guard due to their security lapse and cryptojacked.
- Using browser extensions: Browser extensions are another great way of preventing cryptojacking. Examples of browsers that are designed to block cryptojacking are miner Blocker, Anti Miner, and No Coin among others.
Conclusion
The purpose of this article was to provide a hindsight view of what is cryptojacking, what is crypto mining, and how to detect crypto mining malware. The cryptojacking meaning is a bit complex as it involves technicalities although we tried to make it as comprehensible for our audience as possible. As the demand and value of bitcoin increase, cybercrimes like cryptojacking and ransomware are secretly committed by hackers. Companies need to tighten their data security using a miner blocker. This would help to prevent any unauthorized infiltration into their systems as crypto mining software is flagged as malware.